Stop reinventing the wheel
Reverse engineer mobile applications in a simple way.

Latest news
What makes it different
Static + dynamic + symbolic analysis
Dexcalibur's engine is one of a kind. Indeed, in an autonomous way, it is able to establish correlations between various analysis types results. Based on these correlations, it adapts to the targeted application's specificities to provide you deobfuscation services and customized analysis.
Resilient & Stable
Dexcalibur is designed to analyze highly obfuscated applications. Conscious that a broad techniques diversity exists, we believe Dexcalibur should be stable and resilient to avoid limiting you.
Program Synthesis
Dexcalibur modelizes the target application. From this model, it computes partial program synthesis in order to offer a better view of the program is doing even if the app is obfuscated.
Functionalities
-
Instrumentation's autonomous generation
-
Device's APIs extraction
-
Dalvik bytecode emulation
-
Deobfuscation help
-
System call tracing
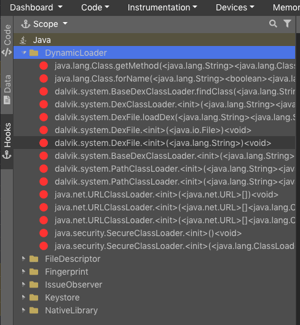 As the application's executions progress, Dexcalibur will comprehend new results and explore new functions. When functionalities linked to your objectives are identified, Dexcalibur will generate a new hook to push further its analysis.
As the application's executions progress, Dexcalibur will comprehend new results and explore new functions. When functionalities linked to your objectives are identified, Dexcalibur will generate a new hook to push further its analysis.
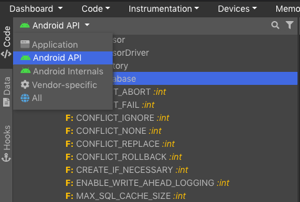 Dexcalibur is able to run an incremental analysis between the Android's API and other APIs available on the device to isolate permissions and specific APIs of a particular model or manufacturer.
Dexcalibur is able to run an incremental analysis between the Android's API and other APIs available on the device to isolate permissions and specific APIs of a particular model or manufacturer.
The virtual machine Dalvik integrated in Dexcalibur offers a behavior close to Android's. It's able to detect implicit exceptions and semantic errors. The execution's context is configurable and can be automatically captured. The VM generate a simplified intermediary representation.
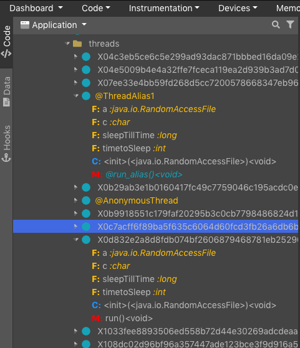 Dexcalibur offers many deobfuscation solutions such as automated renaming, CFG simplification, symbolic execution, types reconstruction...
Dexcalibur offers many deobfuscation solutions such as automated renaming, CFG simplification, symbolic execution, types reconstruction...
Dexcalibur offers an unique multi-architecture system call tracing and hooking functionnality.
A part of the source code has been opened and shared over Github as separate project.
Pro Edition provides a rich API to explore and modify syscall arguments without need to refer to kernel source code.
Tracing features
Interruption tracing
Several kind of calls ( system calls from app, or hypervisor calls and Secure Monitor Calls from os), as well as instruction of target processe can be traced visually . When it is possible, Dexcalibur analyze arguments using a relevant way deduced from platform source code (if it is open-source).
File System monitoring
File system accesses from application are traced. It draws a timeline offering a rich view : file descriptor creation, lookup on FD, read/write with abilities to hook any operations and save or tamper content.
Network monitoring
Network communication (including over HTTPS) can be monitored at application level without modifying network settings of the device and it not requires to bypass SSL Pinning.
NFC monitoring
Commands receipt/sent over NFC by the application can be monitored and tampered at application level. It allows to emulate a kind of virtual relay attack and to spy communication.
Instrumentation features
Java hook generation
It is the most basic feature of Dexcalibur. Browse the application bytecode, select a method, and generate a hook with a single click.
Native hook generation
We think it is one of the coolest feature : explore any native library or process attached to the project, select a symbol or an address, and click 'Generate Hook'. It's ready, your hook will dump (at least) the registers used by the function.
Multiple device
It is a very common use case with smart devices : by instrumenting several devices and app attached to the same project, you can follow the entire workflow !
Multiple processes
By attaching several process to your project, you are able to reverse function involving several processes by instrumenting each side from the same place
Get Dexcalibur today
Let's discuss the best set up for your needs.
